

How The Evolution Of Virus Concealment Is Answered Through Anti-virus Evolution?
Virus V/s Anti Virus Evoulution
Cybersecurity is more on the war-front than you might think it is and anti-virus software is the soldier on guard. We like war movies don't we? So this article is about a war that was conducted among guerillas- "Viruses" and soldiers-"anti-viruses".
This is about how their rivalry grew by the evolution of their methods to fight and strategies to overcome each other's prowess. This is the "Art Of Virus War".
Each day, over 350,000 new malicious programs (malware) and potentially unwanted applications (PUA) are registered. Imagine the kind of data risks and economical losses this can bring to any business.
Thanks to intellectuals and researchers, we have antiviruses that are constantly on guard. So let us begin our war movie and know our soldiers more from inside!
What is Concealment(Cloak)?
Concealment of a virus is like a cloak that hides the viruses or malware from detection. Whenever a malicious software gets installed in a system, it stays hidden/cloaked to start its guerilla war with the system.
Every software possesses a rootkit and viruses use these rootkits to modify the operating system of the host to stay away from detection. Rootkits are software packages provided with the software.
In the case of a mobile application, there are several such techniques used by viruses to stay under the cloak. Some of the restaurant order management system built by developers and hosted by popular platforms, use several tricks to stay concealed and one such trick is by monitoring the motion-sensor input of an infected device, before installing a powerful banking trojan.
This ensures that it does not load on an emulator researcher that searches for detection. This trick works on the principle that motion-sensor on your device will record your movement and register it as you and not some malware.
Evolution Of Cloaks(Concealment Methods):
Concealment of viruses and malware have been evolving over the years now and have seen changes that counter every new anti-virus technique used to detect them. So, let us know out anti-heroes first!
Encrypted Viruses:(1st Gen)
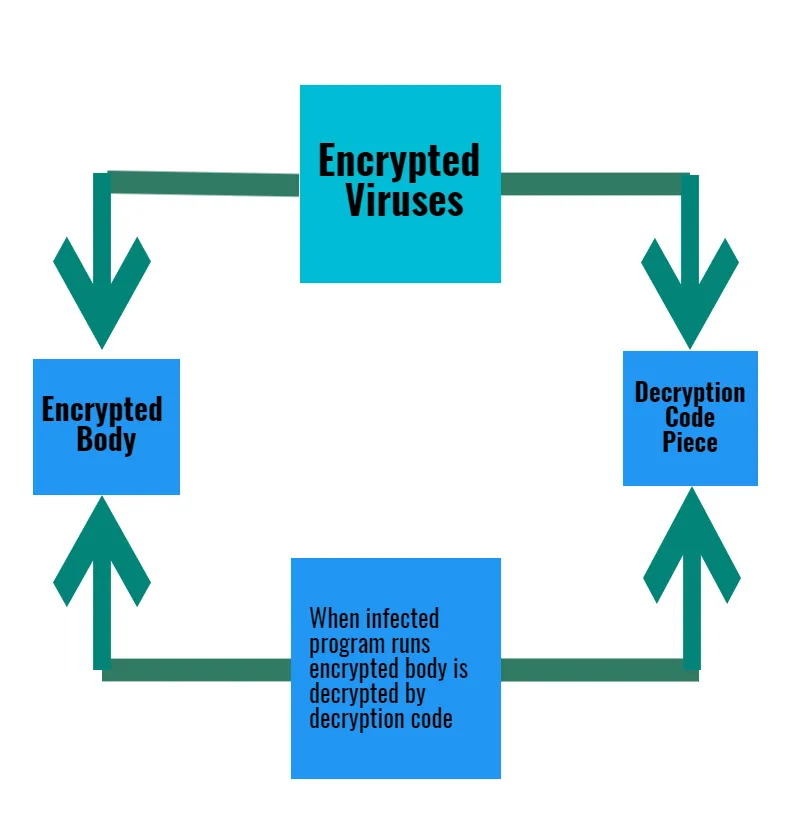
They are considered as one of the most primitive approaches for concealment. Encrypted viruses were designed by changes in the binary codes(In simple terms-"010100110101010") by an algorithm to conceal it. The first encrypted virus was CASCADE back in 1988(https://arxiv.org/pdf/1104.1070). Encrypted viruses are designed with two basic key parts- Encrypted Body and Decryption Code Piece.
Encrypted bodies can infect the program and system, but, it is concealed through a decryptor loop. When an infected program runs, the encrypted body is decrypted by decryption code only to unleash the encrypted body on to the system. This level of encryption helps the virus body to hide from detectors and hexadecimal editors.
Oligomorphic Viruses(2G):
As the 1st generation of guerillas(encrypted viruses) used decryption codes in decryptor loops, it was easy for the then anti-software to detect them. So, virus creators found new ways to create a mutated body for decryptors and a new concealment technique was developed known as Oligomorphic virus.
It substituted the decryptor code with new code by applying several decryptor loops instead of just one. Oligomorphic viruses made the detection process more difficult for signature-based scanning engines. Signatures are considered as the strings used by anti-virus to trace patterns of the virus body for detection.
Polymorphic Virus(3G):
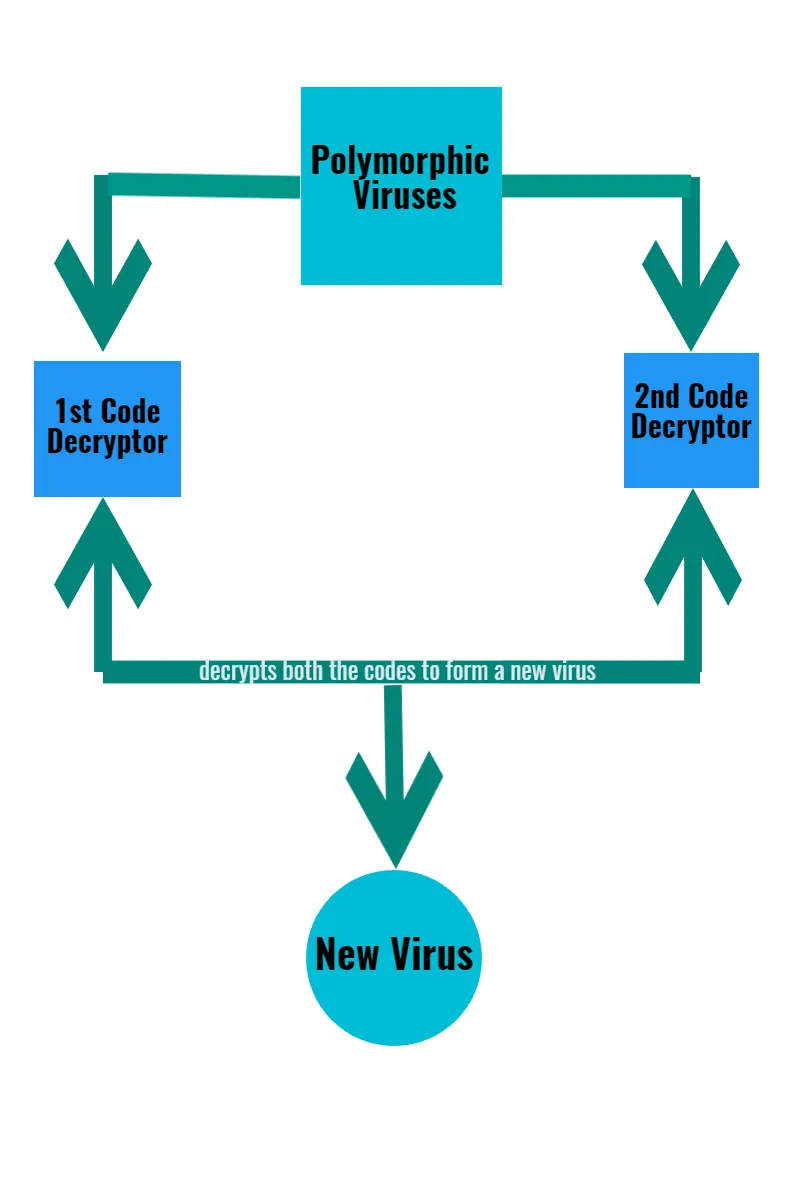
Anti-viruses use signature scanning for detection through small strings known as the signatures and viruses were found based on their signature trace. For, this challenge the virus creators and writers came up with inspiration from nature, just like a chameleon changes its colors, the virus body undergoes transformation and changes the signature to be traced.
Polymorphic viruses consist of two parts with two code decryptors, first code decryptor is coupled by the second decryptor and decrypt a totally new virus with a different signature.
Metamorphic Virus(4G):
With Polymorphic viruses, the original code was easily detectable by the anti-virus software that neglected the signatures produced through the decryptor loops. As virus creators always thrive to create viruses of higher lifespan, polymorphic viruses were a setback. To overcome this setback and counter the scanning anti-virus software, Metamorphic viruses were created.
You can call this a total mutation-like the "Beast" in X-Men Comics. Here viruses undergo a total metamorphism to change their complete body. It also uses a technique of its predecessor- Polymorphic virus, which produces a new decryptor that can be used on the whole virus code to create a new instance.
So we have reached the interval-time, you can go fetch a pop-corn if you are not on a diet choose some butter pop-corns!
Let us begin the second half by knowing more about our heroes.
Evolution of Dagger(Anti-virus Techniques):
Anti-virus softwares began from signature scanning to data analytics techniques of the modern era and the same is reflected further:
1st Generation Scanners:
The earliest scanners searched for patterns and sequences of bytes known as strings or signatures. Every time, a virus is detected, it has a unique signature, which is stored in the database of the anti-virus software. This signature is then used for future detection of the viruses of the same signatures.
Any anti-virus engine of the 1st generation used to scan the binary codes of a file. These scans were for the detection of character strings or signatures that can help identify the virus.
2nd Generation Scanners:
What happened was the obsoletion of 1st generation scanners, due to false-positive results and inefficiency led to the innovation and discovery of the scanners of the 2nd generation.
Smart Scanners:
This was a defense mechanism used against the viruses which concealed under the No Operation instructions(NOP). NOPs were used as the mutated body signatures to avoid detection by the scanners. To this, smart scanners avoided the NOPs and concentrated their focus on the fundamental virus body.
This anti-virus was capable of detecting the Macro-Viruses, written in the text formats. Capability to detect macro-viruses made these scanners quite popular among the computer geeks.
Skeleton Detection:
Developed by the famous Eugene Kaspersky(https://arxiv.org/pdf/1104.1070), it is one of the most popular anti-virus scanners. It does not use strings as checksums for detection purposes. In simple terms, parses the gaps and blank documents of a macro-virus and scans the fundamental(Skeletal) code. By focussing on the fundamental code of the virus body, these scanners reduced the possibilities of deception through the non-instances and metamorphism of the virus body.
Nearly Exact Identification(3G):
It can be termed as a cloning technique, where an element is added identical to the virus body part to track its trace and detect the virus. A single string of virus is replaced by two identical strings. Now, this becomes the source of detection for scanners, Trace of both strings is scanned by scanners and if there were two strings existed in the file- the virus is detected.
The same scanner also calculates bytes value for a particular area of virus body for detection purposes to trace the whole virus body by measure of a particular area.
Exact Identification Scanners(4G):
This scanning method can be called the "Mapping" method. Here the non-variable bytes are utilized by the scanners, ignoring the variable bytes of the virus. It detects the non-variable bytes and maps them all over the virus body to map the virus body completely and easily detect the virus.
Exact identification of the virus can be achieved by this technique and it is possible to exactly discriminate among the viruses and its types.
Heuristic Analysis(5G):
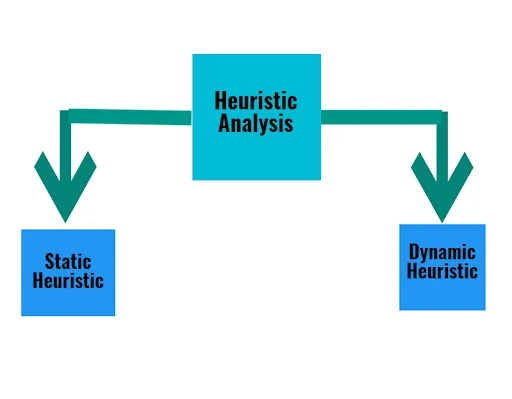
These scanners are based on the latest data analytics methodology. Any heuristic scanner possesses two types of components:
Static Heuristic:
founded by the analysis of file structure and code organization of any virus under the scan. it is based on plain signs and code analysis to recognize the behavior of programs.
Dynamic Heuristic:
Performs CPU Emulation of Virus Code and gathers important data.
Examples of heuristic flags, which shows specific structural problems, may not be included in good executables that are compiled using a 32-bit compiler are as following:
• Possible Gap between Sections
• Code Execution Starts in the Last Section
• Suspicious Section Characteristics
• Suspicious Code Section Name
• Virtual Size is Incorrect in Header of PE
• Suspicious Code Redirection
Ending Scene:
A movie is never complete without a good ending, this was a war of good versus evil. No Kidding!, the evil of malware has been just like a physical virus, which grows more and more innovative with new anti-virus software and methodologies to detect the viruses.
There is no doubt that like the robots in our movies, real-life inventions in Artificial Intelligence and machine learning innovations are changing the way cybersecurity is gearing up to have our systems and networks guarded against the evil of malware.





